Self-signed certificates with Zimly
While it is generally recommended to use certificates issued by a trusted Certificate Authority (CA), such as those from Let’s Encrypt, there may be situations where you need to use a self-signed certificate.
Zimly does not manage certificates directly but supports and trusts user-provided Certificate Authorities (CAs). If you sign your certificate using a CA trusted by Android, Zimly will accept your self-signed certificate.
To use a self-signed certificate, you need to install the root certificate (CA) on your device. This allows your app to trust the server’s certificate when making secure connections.
Before proceeding, consider setting up Let’s Encrypt and a reverse proxy like nginx or Caddy for a more secure and trusted certificate management approach.
Warning: Never share your CA or private key with third parties! Doing so can seriously compromise your device’s security by allowing unauthorized access to encrypted communications.
Generate CA root certificate
For all the following commands, we will assume that the working directory is set to /tmp/zimly-certificates.
mkdir -p /tmp/zimly-certificates && cd /tmp/zimly-certificates
openssl genpkey -algorithm RSA -out ca-zimly.key -pkeyopt rsa_keygen_bits:4096
openssl req -x509 -new -key ca-zimly.key -out ca-zimly.crt -days 30 -subj "/CN=Zimly Test CA"Generate s3 server key and CSR
openssl genpkey -algorithm RSA -out server-s3.key -pkeyopt rsa_keygen_bits:4096
openssl req -new -key server-s3.key -out server-s3.csr -subj "/CN=s3.local"Generate s3 server certificate, signed with Zimly CA
Add alternative IPs and hostnames if needed
Before generating your certificate, consider creating a san.cnf file to specify Subject Alternative Names (SAN).
This ensures that your certificate is valid for multiple domains or IP addresses.
[ v3_ext ]
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[ alt_names ]
IP.1 = 10.0.2.2
DNS.1 = s3.local
DNS.2 = s3openssl x509 -req -in server-s3.csr -CA ca-zimly.crt -CAkey ca-zimly.key -CAcreateserial -out server-s3.crt -days 30 -extfile san.cnf -extensions v3_extPrepare Minio Directory Structure
In this example, we use Minio as the S3 vendor and adapt the directory structure that Minio expects. For reference, see the Minio documentation.
While this structure is vendor-specific, similar configurations should work for other self-hosted S3 solutions.
mkdir minio
mkdir minio/CAs
cp ca-zimly.crt minio/CAs
cp server-minio.key minio/private.key
cp server-minio.crt minio/public.crt
tree /tmp/zimly-certificates
/tmp/zimly-certificates
├── ca-zimly.crt
├── ca-zimly.key
├── ca-zimly.srl
├── minio
│ ├── CAs
│ │ └── ca-zimly.crt
│ ├── private.key
│ └── public.crt
├── san.cnf
├── server-minio.crt
├── server-minio.csr
└── server-minio.keyConfigure certificates in docker compose
Replace the /tmp/zimly-certificates/minio according to your setup.
version: '3'
services:
zimly-minio:
image: minio/minio:latest
ports:
- 9000:9000
environment:
MINIO_ACCESS_KEY: test
MINIO_SECRET_KEY: testtest
volumes:
- /tmp/zimly-certificates/minio:/opt/minio/certs/
command: server --certs-dir /opt/minio/certs /data
Copy and Import CA Certificate to your Device
To add the CA certificate to your Android device, follow these steps:
1. Transfer the CA Certificate
Use adb or any other method to copy the certificate to your device:
adb push /tmp/zimly-certificates/ca-zimly.crt /sdcard/ca-zimly.crt
Alternatively, you can transfer the file manually via USB or a cloud storage service.
Make sure to use an encrypted transfer method to protect the integrity and confidentiality of your certificate.
2. Install the CA Certificate in Android
- Open Settings → Security → Encryption & credentials.
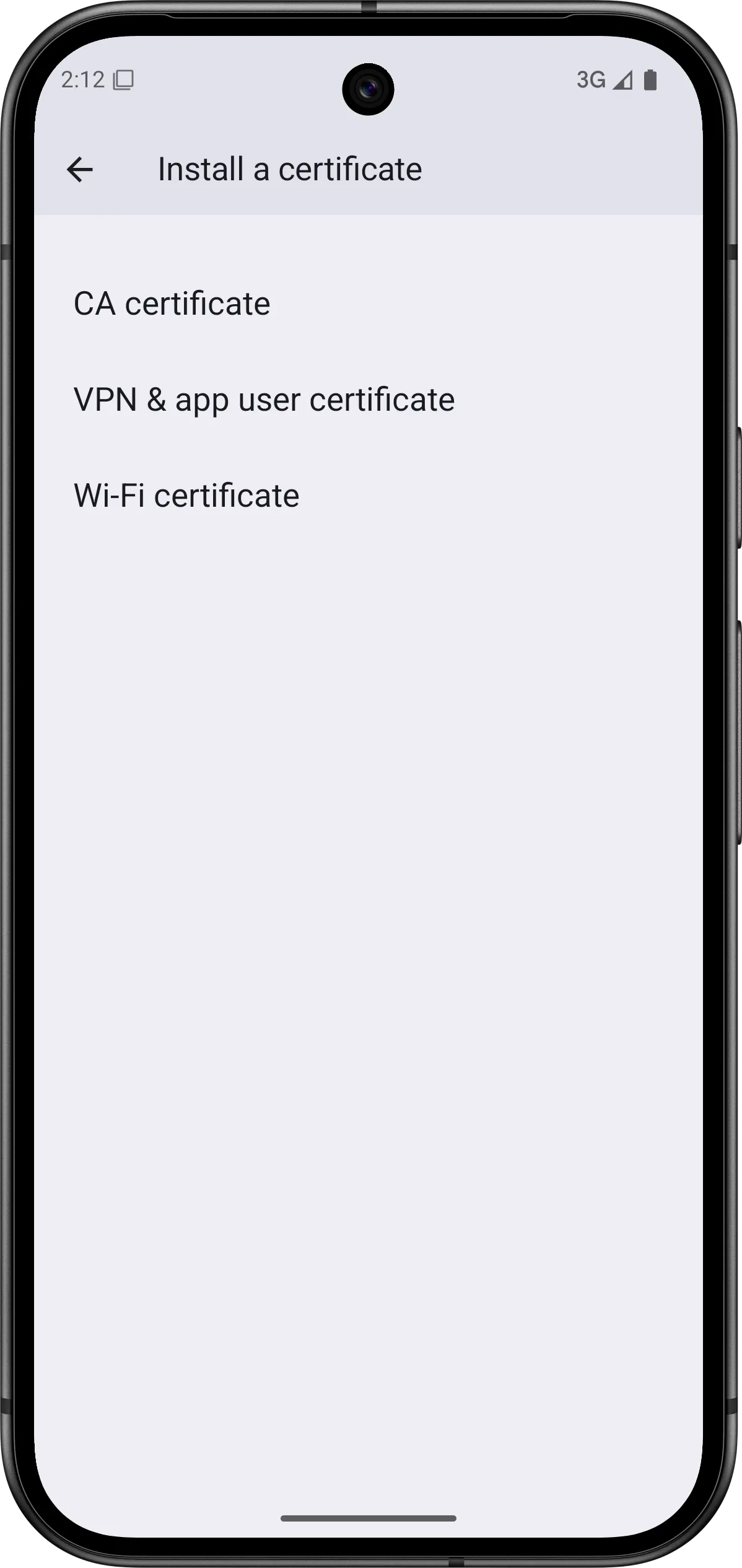
- Select Install from storage (or Install a certificate).
- Choose CA certificate and locate ca-zimly.crt in your device storage.
- Confirm the installation when prompted.
Verify that Android recognized the CA certificate:
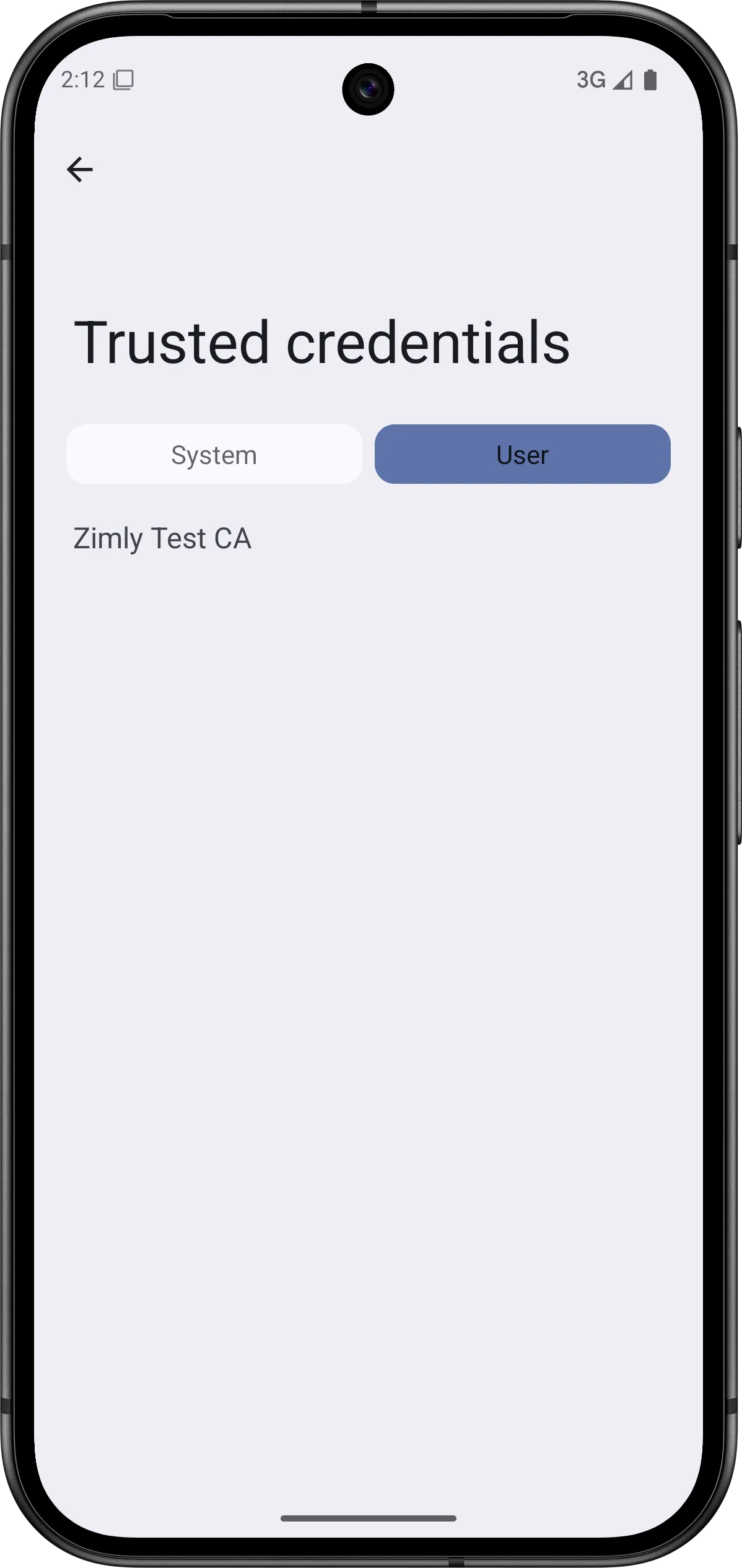
Once installed, Android will trust any certificates signed by this CA.
Use it in Zimly
Configure your S3 endpoint to use https://, ensure you use a host or IP that was added as a SAN entry above.
